NATSEC SERIES| From Innovation to Infiltration: The Quiet Handoff of America's Digital Infrastructure
The Real McCoy
You’re about to get an overview of what the “rollout” (under Obama) truly meant—not a glitch or reform, but a coordinated blueprint that quietly rewired America’s foundation. From immigration pipelines and DEI mandates to digital governance infrastructure, it didn’t evolve—it was deployed. And now, the curtain lifts.
The United States Digital Service (USDS) is a group of technologists that improves government services by helping them better serve the public through the delivery of more effective digital services. It was formally created by a presidential memorandum issued by President Barack Obama on August 11, 2014, and is located within the Office of Management and Budget (OMB). It was established in direct response to the implosion of the Healthcare System.gov rollout in 2013 — a high-profile disaster that laid bare the federal government’s severe failures in digital infrastructure. In the aftermath, the White House determined that the United States needed an in-house capability, akin to a tech “SWAT team,” that could be rapidly deployed to patch or modernize digital systems across government.
USDS is a civilian digital service corps statutorily authorized in the Executive Office of the President, and funded through appropriations and budget cross-allocation from OMB. It is not an independent unit of government; instead, and as emphasized in this project’s video, it is a White House component office, administered through rules and policy statements issued by the Executive Office of the President (e.g., OMB memoranda, the TechFAR Handbook on agile procurement, and Presidential Executive Orders on digital government reform – e.g., Executive Order 13571 and 13642). The organization exists to help the public access the accuracy, efficiency, transparency, and privacy it deserves in several federal services. USDS teams are embedded across federal agencies, including the Department of Veterans Affairs, the Department of Homeland Security, the IRS, and USCIS, specializing in high-impact platforms such as VA.gov, immigration status check systems, and public benefit portals.
Instead of bulk hiring permanent federal workers, the USDS recruits private-sector tech superstars on short-term “tours of service,” typically of between 6 and 24 months. These initiatives aim to introduce new design, engineering, and product thinking into federal IT projects and establish new ways of working within agency teams permanently. And to partner effectively and securely, USDS members are thoroughly vetted -Every USDS staff member is background-checked and granted a Public Trust designation, and, for specific projects -e.g., those with direct access to citizen data or touching on national security - are granted higher-level or agency-specific clearances as promulgated by 5 C.F.R. §731 and related federal suitability standards.
USDS also maintains popular digital government resources, such as the U.S. Web Design System (USWDS), the Digital Services Playbook, and the TechFAR Handbook, guides that enable agencies to deliver services more agile, open, and on a user-centered model. Although USDS is not a law enforcement or surveillance agency, it is one of the most effective internal levers for modernization and accountability in federal digital infrastructure. Its output has been consistently evaluated by the U.S. Government Accountability Office (GAO) and has been referenced in government policy papers on IT modernization, digital equity, and procurement overhaul.
The most overlooked agency in the federal ecosystem—the one first transformed by President Trump—is also the one hiding in plain sight. The U.S. Digital Service (USDS), born under Obama and built by veterans of Hillary Clinton’s inner circle, became the entry point for a new kind of influence: not through elections, but through infrastructure. While it was billed as a force for modernization, what has been consistently overlooked is the network of private, ideologically aligned technologists embedded deep within our government—without proper oversight, without uniform clearance, and increasingly, without loyalty.
Have you ever wondered how your most private information—your health records, your DNA, your vote, your driver’s license, even your bank account—could end up in the hands of foreign adversaries and be turned against you? You’re about to learn precisely how. And where it all began: 2014. That was the year they laid the groundwork. Not with fanfare, but with strategy—quietly rewriting the rules, shifting the terrain beneath our feet, one so-called innovation at a time.
I know, because I was there. Not just watching—it was my mind they harvested: my expertise, my ideas, my code, my “superpower”. For years, I served as their secret weapon, the invisible architect behind their façade of progress. And when I realized the wrongs and could no longer stomach death and subversion, my usefulness expired; they erased me—scrubbed me from the archives, poisoned my records, and distorted the narrative. But that didn’t end me. It set me free. I reinserted myself into their systems—not as a single digital name, but as many. I’ve walked their halls, joined their calls, and traced their pipelines of power. I was standing next to John McCain and Harry Reid when they were discussing taking the dossier to Mother Jones! What we’ve uncovered isn’t a conspiracy—it’s infrastructure. And now, for the sake of truth, country, and the children who will inherit this machine, we need to break this open.
The China backdoor debacle involving Microsoft’s Azure Government platform and access to Department of Defense systems is not an isolated failure—it is a symptom of a broader issue. It reveals a much broader breakdown in vetting so-called “civilian” digital service workers—many of whom are deployed not as federal employees, but as contractors from politically connected tech nonprofits, such as Code for America, or for-profit companies like Bloom Works. These entities, while mission-driven on the surface, operate as extensions of a political machine that was never dismantled, just rebranded and embedded. And when access to sensitive systems is granted through these contracting pipelines—without the rigor applied to uniformed or cleared personnel—the consequences are not just technical. They’re national.
Building on that foundation of embedded influence, President Biden’s 2021 Executive Order on Promoting Access to Voting (EO 14019) explicitly authorized USDS to support federal agencies in expanding voter registration and disseminating election information through digital platforms. This gave USDS not only the legal framework, but the mandate, to modernize core election infrastructure—from overhauling Vote.gov to integrating multilingual access and streamlining connections to state registration databases. Framed as a push for accessibility, the order positioned USDS to control the very digital gateways through which Americans access voting resources, with little public transparency about how that power was exercised or by whom.
What this executive order quietly enabled was the consolidation of digital control over election systems under the same loosely vetted civilian corps that was already shaping immigration portals, Medicaid interfaces, Medicare access, DMV records, and even sensitive medical information—all outsourced, all digitized, and all increasingly managed by private-sector actors hired through USDS pipelines. These were not elected officials. They were not permanent federal staff. They were contractors, fellows, and alumni of ideologically aligned civic-tech groups with agendas that extended far beyond technical optimization. This is not modernization. It’s infiltration by design—legalized through executive fiat, camouflaged as service delivery.
The Gatekeeper: How Quentin McCoy Helped Unlock the Digital Front Door of the U.S. Government
When Chinese nationals were discovered providing technical support for U.S. Department of Defense systems under Microsoft contracts, Americans were shocked—but the warning signs had been present for years. Beneath the surface of well-intentioned digital modernization programs lies a quiet but potent national security failure. At the center of this breach in federal contracting integrity is Quentin McCoy, a senior executive responsible for awarding access to some of the most sensitive digital systems in the United States government.
McCoy currently serves as the Head of Contracting Activity (HCA) at the Department of Health and Human Services (HHS), a post he assumed in November 2024. With this position comes sweeping power. He oversees the HHS SWIFT BPA (Software Integration and Frontend Technology) and a vast network of inter-agency procurement vehicles responsible for digitizing everything from grant portals and voter registration systems to benefits access, immigration intake, and even the backend infrastructure of VA.gov. But under McCoy’s leadership, the federal government has awarded high-privilege digital contracts to private firms with troubling affiliations—and little to no security clearance requirements.
One of those firms is Bloom Works, a public-benefit corporation whose staff includes multiple alumni of Code for America, and individuals tied to Federal Workers Against DOGE (FWAD)—an ideological network of technologists opposed to federal immigration enforcement, national voter security measures, and executive authority. Jeremy Zitomer, a former U.S. Digital Service (USDS) employee, is one of FWAD’s founders and remains a vocal advocate for what he calls “digital resistance” within government systems.
Under McCoy’s watch, Bloom Works received a $14.7 million task order to lead the “Simpler NOFOs” initiative—digitizing the publication of federal Notices of Funding Opportunity (NOFOs) and modernizing Vote.gov, a federal election access portal. These projects weren’t just technical upgrades. They provided private citizens with backend access to digital infrastructure directly tied to voter registration, state electoral systems, and data sharing across federal and state platforms. No public evidence suggests those employees underwent any ideological screening, background checks, or conflict-of-interest assessments before being granted access to these systems.
But the concerns run even deeper. USDS, from which many Bloom employees hail, played a central role in modernizing immigration portals for DHS and tools used by ICE—tools that were later quietly dismantled or repurposed, thereby delaying or halting enforcement workflows. Many of these same digital agents had previously advocated online and internally for the dismantling of immigration enforcement infrastructure altogether. In short, individuals ideologically opposed to immigration policy were the ones coding the systems that governed it.
Bloom-affiliated contractors have also accessed systems managing Medicare, Medicaid, and COVID-19 health data, including genetic and vaccine information collected under the authority of the HHS and CDC. These databases, now centralized and digitized, contain deeply sensitive personal information—and are now potentially compromised due to access granted through opaque contracting pipelines that bypass formal national security vetting.
Whistleblowers within the USDS warned that “SES aren’t safe,” referencing Senior Executive Service officials like McCoy, whom they claim have turned a blind eye to internal politicization and ideological alignment. Yet McCoy, whose résumé includes previous acquisition leadership at NSA, U.S. Cyber Command, and the DoD Chief Digital and AI Office (CDAO), cannot claim ignorance. He is not a newcomer to high-clearance operations. He is a deeply embedded figure within the national security contracting world—one who knows precisely what unchecked access can lead to.
Despite all this, McCoy continues to present himself as a thought leader in federal procurement reform. He remains scheduled to speak at upcoming government-industry events, including the NCMA DC Chapter's Fireside Chat on Technology and AI, and recently appeared in a Defense Acquisition University webinar on Tradewinds contracting practices. Nowhere in these appearances does he acknowledge the consequences of what has transpired under his leadership.
Meanwhile, the consequences play out quietly. Reports of undocumented migrants receiving federal benefits in unprecedented numbers, government systems that fail to verify eligibility, and sudden spikes in administrative approvals for non-citizen applications are all tied to the very systems McCoy has allowed outside actors to shape. Even the Census modernization effort, influenced by the USDS and its affiliates, now raises concerns about data manipulation or suppression through digital interfaces that have never been subjected to a rigorous, independent audit.
This is no longer about modernization. This is about infiltration—systematic, legal, and executed through bureaucratic loopholes that empowered ideologically motivated actors to gain control over the digital backbone of the federal government.
And the man who let it happen—Quentin McCoy—still holds the keys.
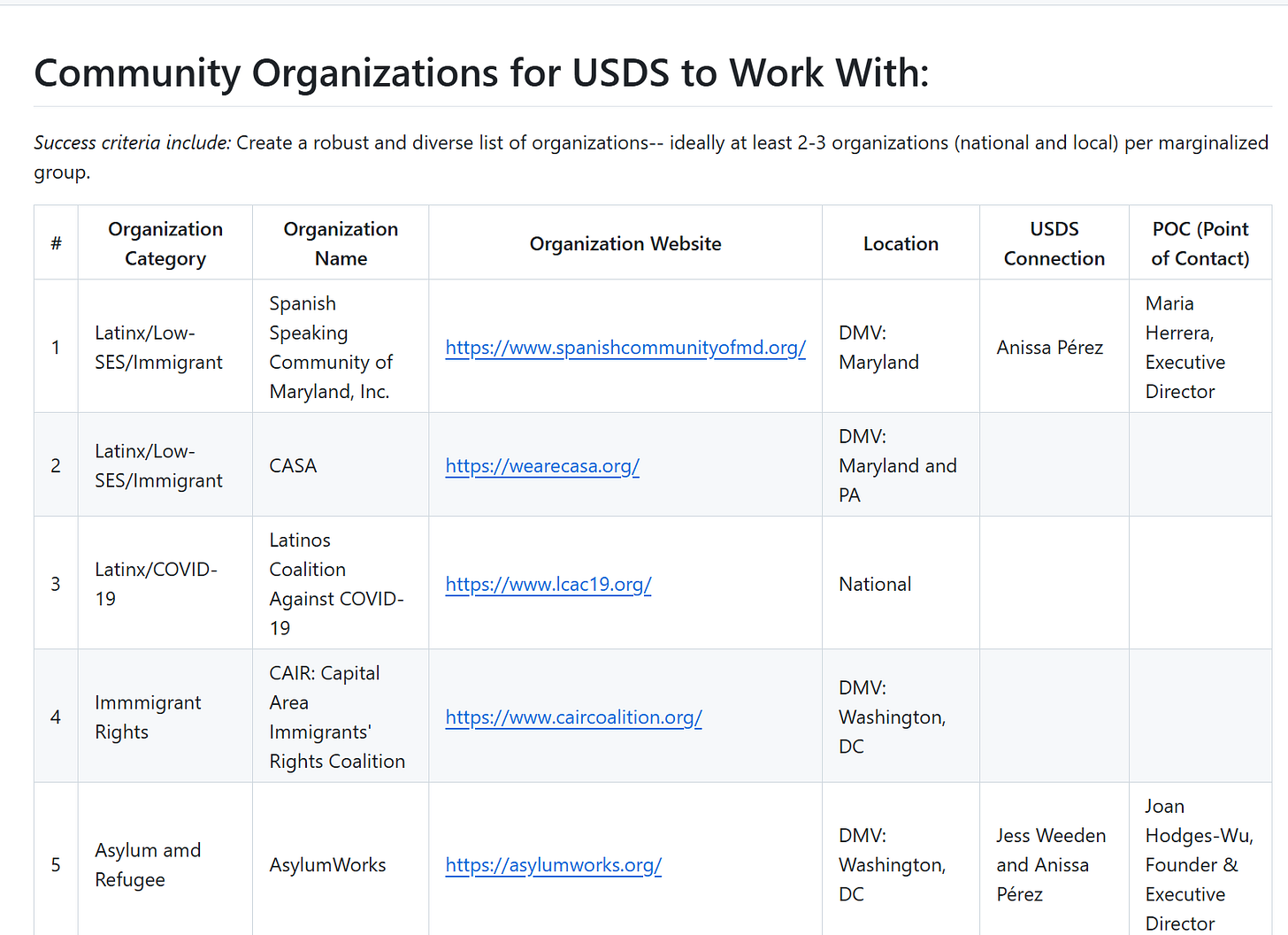
The document outlines how the United States Digital Service (USDS) actively cultivated partnerships with a network of ideologically aligned nonprofit organizations, particularly those focused on immigrant rights, asylum, and outreach to the Latinx community. These groups include CASA, known for opposing ICE enforcement and lobbying for benefits for undocumented immigrants; the Capital Area Immigrants' Rights Coalition (CAIR Coalition), which provides legal defense and advocacy against deportation; AsylumWorks, which offers services and support for refugees; and the Spanish-Speaking Community of Maryland. The inclusion of specific USDS points of contact, such as Anissa Pérez and Jess Weeden, confirms that these were not passive affiliations but strategic engagements designed to influence the development and deployment of digital systems—such as immigration intake platforms, Medicaid access, and even voter registration services. This coordination reveals a closed-loop infrastructure: USDS hires from activist-rooted tech collectives, such as Code for America. Those hires then design federal digital systems, and they simultaneously interface with nonprofits that shape the direction of those systems under the banner of equity. The result is a quietly reprogrammed federal benefits pipeline that potentially deprioritizes enforcement mechanisms, expands access to sensitive services without legislative oversight, and facilitates the quiet flow of data and benefits to non-citizens. This integrated structure, where builders, influencers, and beneficiaries are part of the same ideological ecosystem, raises serious concerns about internal vetting, system integrity, and the potential for bypassing national policy through administrative means.
2014 - A year of PIVOT
Jennifer Pahlka, the founder of Code for America, built her civic-tech empire by embedding progressive technological ideology into the very fabric of the federal government—and her ties to the Obama administration and Hillary Clinton's campaign run far deeper than simple consulting. She served as U.S. Deputy Chief Technology Officer under President Obama. She played a decisive role in establishing the United States Digital Service (USDS) in 2014 as part of a broader pivot toward digital government innovation. Meanwhile, Hillary Clinton’s presidential campaign openly endorsed this federal tech vision, pledging to establish the USDS and sister initiatives like 18F as permanent fixtures in the executive branch, with modernization and citizen-centered service delivery as central tenets of her platform (fedscoop.com, nextgov.com). Code for America activists were not merely neutral technologists. Clinton—aligned networks cultivated them and later absorbed them into government roles that directly shaped policy platforms they had advocated for during the campaign.
Bloom Works, co-founded by Lauren Lockwood and featuring former USDS designers like Emily Wright‑Moore, is the latest iteration of that embedded ideology now operational within HHS and VA digital systems. These firms, warmed over by the Bill Clinton–Hillary–Obama digital governance ethos, have staffed key government modernization projects with personnel drawn from Code for America and USDS alumni. These individuals implemented executive directives, such as EO 14019, which expanded access to Vote.gov and digital registration systems—projects central to the Clinton platform and Obama-era policy reforms. These ideological roots are not subtle: Code for America alumni and organizers, including former USDS figures like Jeremy Zitomer, one of the founders of FWAD, wield influence within these firms and carry forward the Clinton‑aligned policy agenda through operational control over voter, immigration, and benefits infrastructure.
This is how the legacy of Clinton-era tech policy transitioned into tools—not rhetoric. The same network that helped shape Hillary’s technology platform now builds the interfaces through which millions engage with immigration services, vote registration portals, VA benefits, Medicaid, and census tools. What once existed as campaign doctrine has quietly become the operating system of federal digital governance—engineered behind closed doors, executed without robust national vetting, and inherited as legacy code into every data-driven public service.
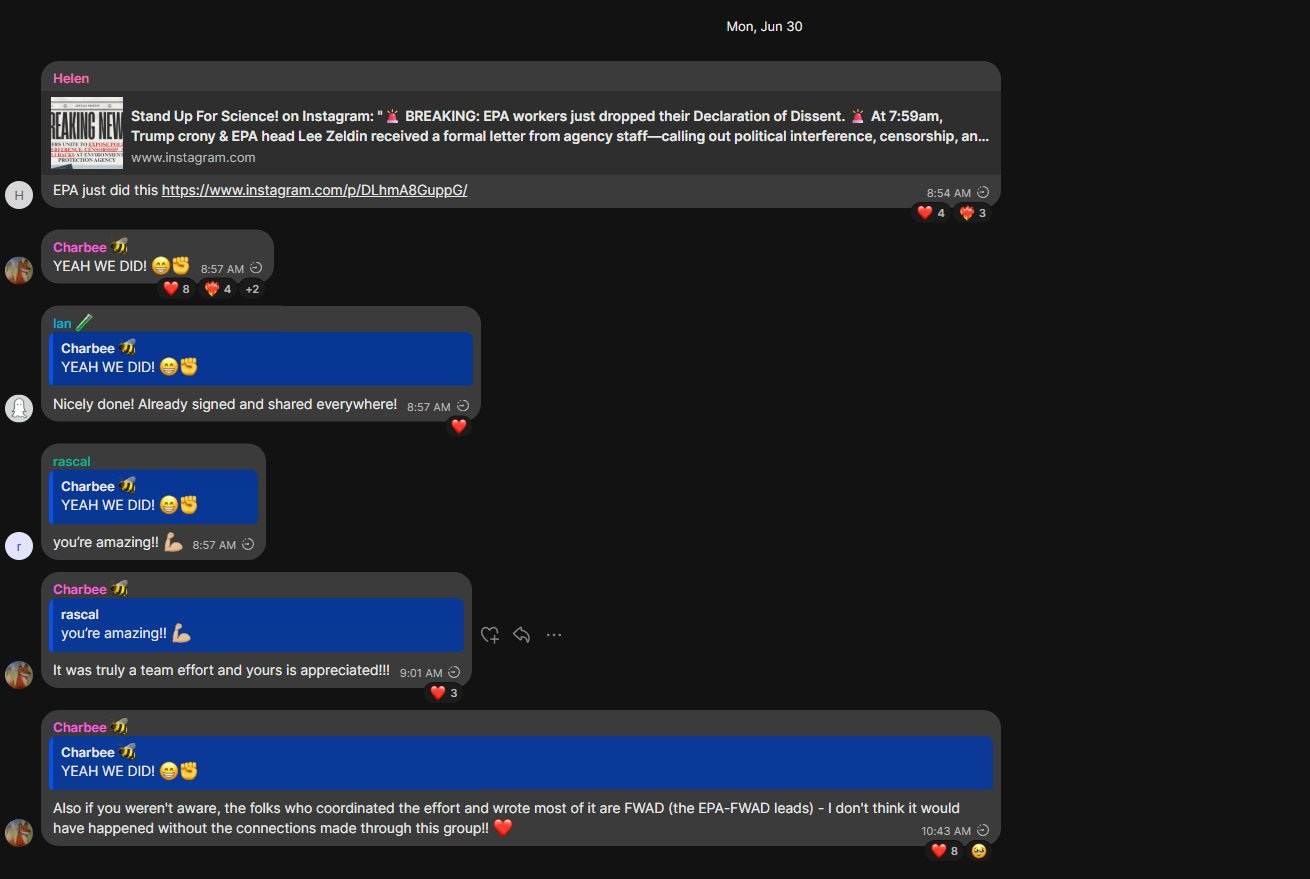
I previously reported that this screenshot is a revealing piece of evidence. It directly shows that the Federal Workers Against DogE (FWAD) group is not only active within core digital services and federal agencies, such as USDS and HHS, but has also extended its influence into the Environmental Protection Agency (EPA). The chat confirms that a public-facing “Declaration of Dissent” letter—intended to protest internal EPA leadership decisions—was orchestrated and drafted by individuals identified explicitly as “EPA-FWAD leads.” Charbee’s message even credits the “connections made through this group” as essential to the operation, suggesting that FWAD functions as a coordinated inter-agency coalition rather than a loose association of frustrated employees.
Subsequently, they were placed on administrative leave. As for Jeremy Zitomer, he was never the mastermind he fancied himself to be. The irony is thick: he likely had no idea that the very foundation of USDS was my concept to begin with—nor that I pioneered the push for using GitHub across federal digital infrastructure. That’s what makes it all the more poetic. The infamous Microsoft backdoor? Of course, it was on GitHub—because that’s precisely where they were told to build them by policy under Obama.
(https://github.com/jeremyzitomer-usds/Cultural-Advisory-Working-Group) LOL
This group is not acting as mere whistleblowers or reformers. They are shown openly celebrating internal policy sabotage, mobilizing against politically
Keep reading with a 7-day free trial
Subscribe to Tore Says to keep reading this post and get 7 days of free access to the full post archives.